seculution Application-Whitelisting
How's that work?
Why is the seculution antivirus solution so easy to use? Which components enable superior protection without deep learning, heuristic analyses or updates of virus definitions?

Why is the seculution antivirus solution so easy to use? Which components enable superior protection without deep learning, heuristic analyses or updates of virus definitions?
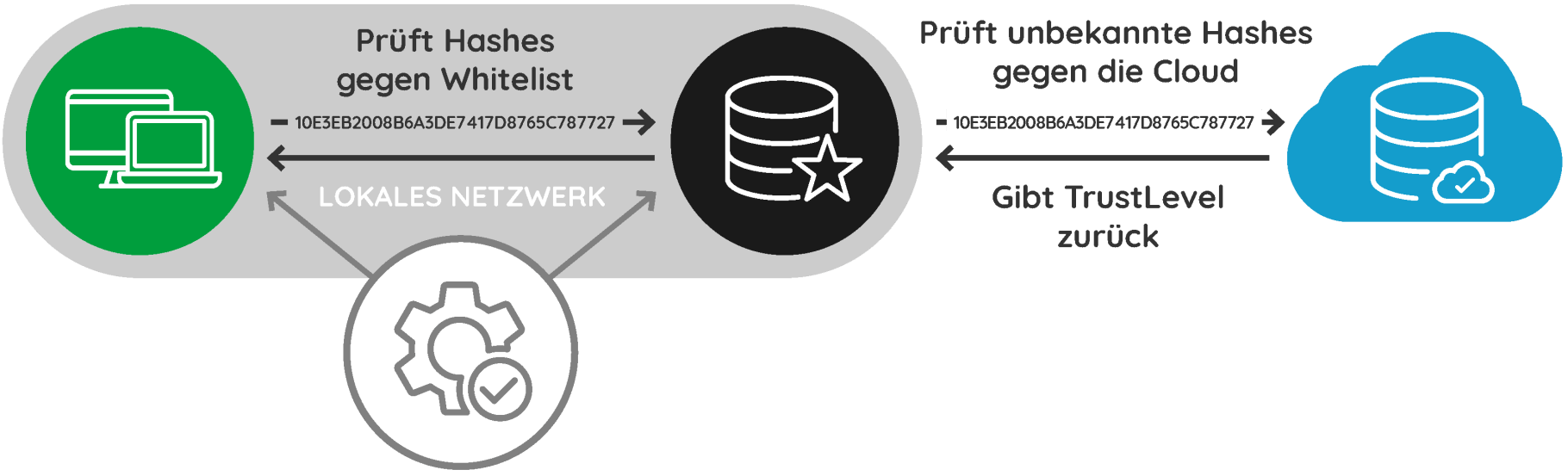
On every computer that is secured with seculution, the agent generates a hash from the binary data of the applications to be started. This hash is used to uniquely identify the starting program.
If the hash is not on the whitelist, the execution of the software is refused.
On every computer that is secured with seculution, the agent generates a hash from the binary data of the applications to be started. This hash is used to uniquely identify the starting program.
If the hash is not on the whitelist, the execution of the software is refused.
seculution maintains a cloud-based database with hashes of trustworthy software in a German computer centre.
seculution assesses how trustworthy a hash is with so-called trust levels. The TrustLevel database is maintained exclusively by employees of seculution GmbH and provides a good TrustLevel for more than 99% of queries.
In the AdminWizard, you maintain the objects in the whitelist and can specify which application and which USB device can be used by which user.
You configure the agent and the server here.
In the AdminWizard, you maintain the objects in the whitelist and can specify which application and which USB device can be used by which user. With TrustLevel, every software is clearly evaluated. Malicious code has no chance of getting on your whitelist!
Even before you receive the message about a software update, it is already known and evaluated in the seculution cloud. You always benefit from the latest data and nothing is blocked.
Only 100 milliseconds pass from the request to the approval. This is still 3 times slower than the direct query, but still not noticeable for users.
Sit back and focus on other tasks. Your whitelist takes care of itself.
Guaranteed safe!
No matter when software is to be started, the agent detects this process and verifies the authenticity of the requested software before starting it.
Only if a software can be uniquely identified by its hash the agent allows the execution. No exceptions.
Even without being able to connect to the seculution server, the agent protects you. Hashes held in a local cache are used as offline backups of your whitelist.
The entire communication between agent and server is secured via SSL (TLS). Data traffic is exclusively caused by the query of programs to be started.
Your whitelist stays yours. The seculution server is located in your network, under your control.
No delay even with many requests at the same time. Scalable through the use of multiple synchronised servers.
Our specially hardened complete server system. Maintenance-free and stable.
The seculution Server is a preconfigured virtual machine that is available to you via download. Add it to your datastore, done!
From Agent-Configuration over Active-Directory replication to whitelist maintenance and automation, the AdminWizard is your tool.
Keep the overview without the need to manually manage the system. Intelligent classification and clear rule views make it possible.
Reduce manual work to a minimum and use the automated reading of trusted hashes during operation.
Keep track of secured clients and pending agent updates. Our integrated agent deployment makes this task easier for you.